
- Why Cleafy
- Solution
- Intelligence
- Resources
- Company
- Get in touch
 Get in touch
Get in touchIn 2023, Account Takeover (ATO) was confirmed to be among the most harmful types of fraud for online banking customers. At Cleafy, we have seen that 90% of fraud attempts are still conducted via Account Takeover, and our forecasts expect this number to stay flat in 2024. Banks and financial institutions have always been the highest priority targets of ATO attacks, as cybercriminals aim to make immediate financial gains from their illegal activities.
An intricate and growing threat is On-Device Fraud (ODF). This fraud presents a multifaceted challenge for anti-fraud teams within the banking sector, as it involves fraudulent activities initiated directly through the victim's device. Unlike traditional methods of fraud, ODF reduces the presence of conspicuous risk indicators during browsing sessions, rendering conventional anti-fraud countermeasures largely ineffective.
This emerging threat has been made possible through the capabilities afforded by over 80% of modern Android banking trojans such as Vultur, TeaBot, and SpyNote. At the core of this capability lies the concept of remote control, which enables Threat Actors (TAs) to execute ODF scenarios. Each malware family executing remote control functionality may employ distinct implementation flavours, reflecting the varying skills and knowledge of the developers behind them.
Readers must understand that the challenge posed by ODF extends far beyond a single banking trojan like Copybara, the focus of this report. Our findings underscore the broader scope of this threat landscape, as we have traced the entire fraud chain orchestrated by responsible TAs. This investigation will give readers the full spectrum of their tactics, techniques, and procedures (TTPs), from the initial Social Engineering components (such as phishing and vishing) used to initiate the attack to the distribution of Copybara for device infection and the meticulous management of these attack phases to ensure the success of their campaigns.
The following table represents a summary of the TTP behind Copybara campaigns:

The following diagram provides a high-level overview of the technical components involved in TA fraud operations.

On top of this fraud operation architecture, TAs exploit Social Engineering techniques for distributing the Copybara banking trojan, which typically involves smishing and vishing techniques, leveraging native-speaker operators. In particular, several samples reveal TAs distributing Copybara through seemingly legitimate apps, utilizing logos of well-known banks and names that sound authentic, such as “Caixa Sign Nueva”, “BBVA Codigo”, “Sabadell Codigo”.
According to data retrieved during our investigation:
TAs are interested in 3 countries: Spain, Italy, and the UK.
Phishing has evolved into a sophisticated art form in cybercrime, leveraging deceptive tactics to trick individuals into revealing sensitive information. Nowadays, many successful phishing campaigns leverage tools called "phishing kits." These kits are pre-packaged sets of malicious tools and resources meticulously crafted by TAs to streamline and amplify their fraudulent activities.
A phishing kit is a collection of malicious assets and scripts designed to replicate legitimate websites, often mimicking the login pages of banks, financial institutions, or other trusted platforms. These kits are constructed to deceive unsuspecting victims into divulging confidential information such as usernames, passwords, and phone numbers.
The deployment of phishing kits serves several purposes for cybercriminals engaged in fraudulent activities, especially those centered around banking fraud:
Our investigations unveiled an additional C2 framework dubbed "Mr. Robot". The name “Mr. Robot” has been taken according to the logo present on the login page of the web panel.

What sets this C2 framework apart is its capability to handle multiple phishing campaigns concurrently. It allows TAs to orchestrate tailored attacks on distinct financial institutions simultaneously. Each phishing campaign, equipped with unique phishing kits, is designed to mirror the targeted bank's online interface.

According to the source code of Mr. Robot C2, the authors decided to leave a standard database, such as MySQL, to store only some of the fraudulent data collected during their campaigns. Instead, their approach was based on the usage of SleekDB, a NoSQL database implementation using pure PHP that stores data in plain JSON files, as shown in the following Figure.

The consequences of this approach are crucial since all the data appears to be saved in plain text, in JSON format, and inside the web server. Data can be easily accessible without authentication if the path is known.

Despite these weaknesses encountered during our analysis, TAs deployed several layers of countermeasures against web crawling and scraping techniques, widely typically adopted by cybersecurity firms and vendors. The following paragraph will explore how TAs try to evade detection and domain takedown actions.
Nowadays, multiple Threat Intelligence vendors have embraced proactive measures to identify phishing websites, newly registered and, in specific contexts, soon-to-be activated. On the other hand, TAs put effort into developing evasion techniques to avoid a quick detection of a newly registered phishing domain.
Typically, modern phishing kits adopt multiple anti-detection techniques, including:
The following Figure summarises all the primary anti-evasion techniques adopted, starting when a potential new victim follows a malicious link set up by TAs.
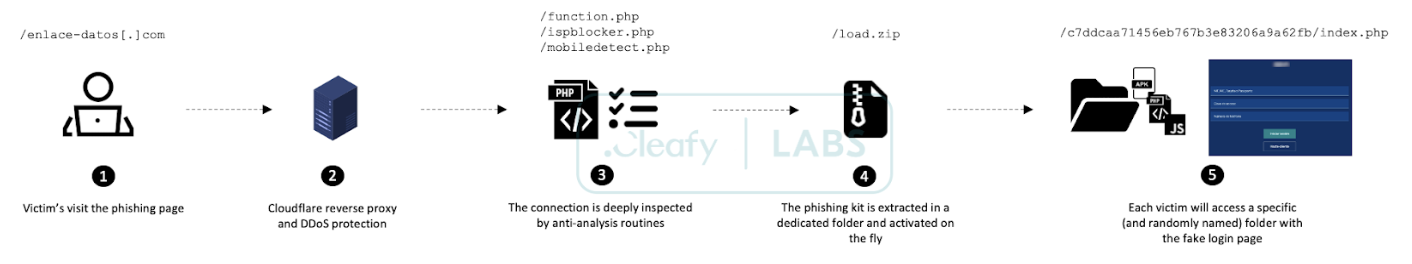
Since the primary focus of this fraudulent campaign is the clientele of retail banking institutions from specific geographical areas (Italy, Spain, and the UK), filtering out all the connections except the ones coming from a mobile device is a pretty standard technique adopted by various TAs. Most individuals nowadays engage in home banking activities through their mobile devices, making them lucrative targets for TAs.

If all the checks are successfully passed, the originating connection will be considered “a potential new victim”, so the phishing login page can be shown accordingly.
As shown, TAs adopted a dynamic routine to extract all the necessary files for their phishing attempt at run-time. With this method, each victim will be redirected to a specific subfolder and randomly named where the phishing kit has been extracted.

The following is an example of an active phishing kit leveraged by this TA, which is composed of three simple steps:

All the collected data are usually sent back to a dedicated Telegram group, if set, and stored on their C2 panel. From here, operators can easily manage all victims' data inserted in the current phishing page.
The next step is a vishing approach to the victims. Fraud operators leverage native speakers to get a direct connection via phone, typically spoofing a valid number of the targeted banking institution and introducing them as an anti-fraud / security team.
According to their panel, a dropdown menu has been created to help fraud operators keep track of the state of each victim:

In this section, we provide a tour of the main features of the Copybara botnet, starting from the functionalities offered through the associated C2 (Command and Control) web panel.
In botnet operations, C2 web panels provide attackers with a centralised interface to manage and control compromised devices. These panels are pivotal components in the infrastructure of botnets, offering attackers a range of functionalities to execute and oversee their malicious activities.
Furthermore, web panels facilitate data collection from compromised devices, including system information and credentials, enabling analysis and exploitation for further malicious activities. Lastly, botnet controllers leverage web control panels to monitor the health and performance of their botnet, tracking the number of active bots and their geographic distribution.
Understanding the capabilities and functionalities of web control panels is crucial for comprehending the threat landscape posed by botnet operations. Analysts can gain deeper insights into attacker tactics, techniques, and procedures (TTPs) by dissecting these components, enhancing their ability to effectively mitigate and counteract such threats.
Copybara leverages a C2 panel named “JOKER RAT”. Starting from its dashboard, the panel displays the list of all the infected devices and their geographical distribution over a map, with the feature called “Live MAP”, as shown in the following Figure 11.

This dashboard can also retrieve basic information about the infected devices, such as the device name, OS version, and IP address. With this data, TAs can easily “triage” the infected devices by country or determine which victim is online/offline. A “notification mechanism” is also triggered whenever a new device is infected.
As shown in the following Figure 12, for each infected device inside the panel, TAs can perform different actions, in particular:

When the “Silent Connect” button is clicked, a new page is opened, and TAs can collect additional data and perform fraudulent actions on the infected device.
In the Android banking trojan context, this feature is also known as VNC, which enables the attacker to view and manipulate the screen of the compromised device remotely. This level of access allows them to carry out various fraudulent activities, including on-device frauds (ODF).
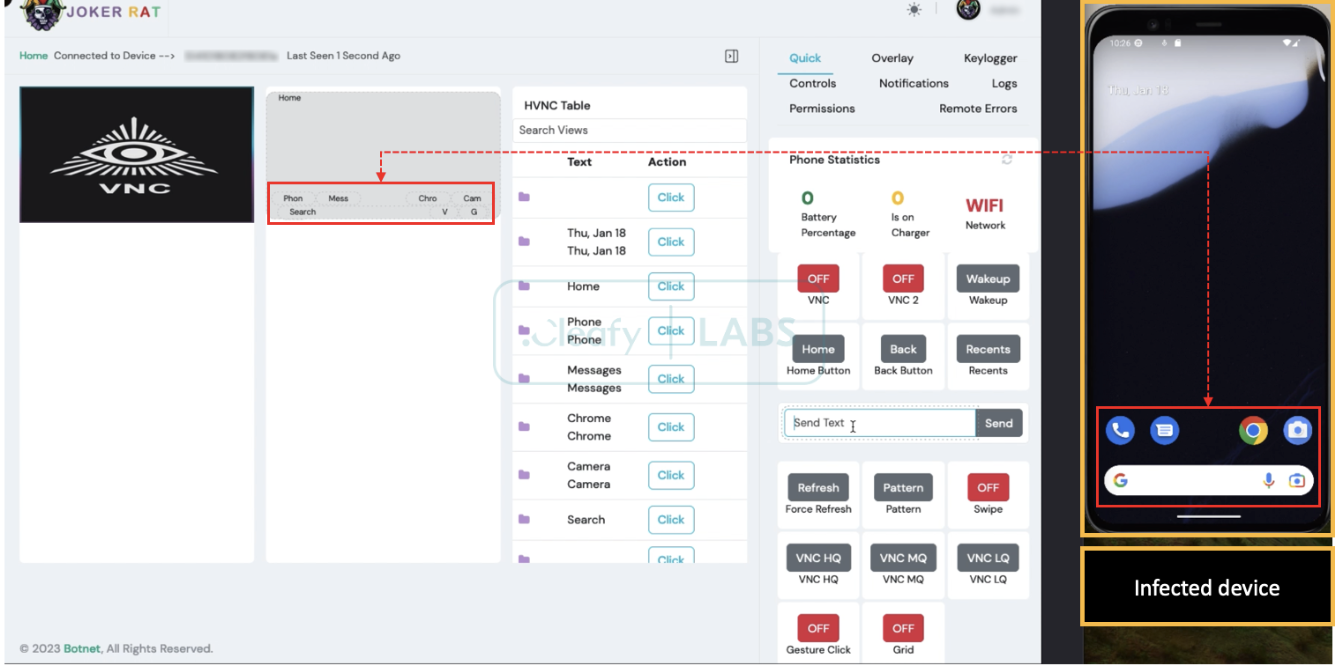
Once the user accepts the Accessibility Service popup during the installation phases, the malware can record every activity done by the user on the compromised device. The attacker can observe them in real time on the C2 panel. In particular, the TAs can observe:


Another way to steal the banking/crypto credentials is through the well-known overlay attack. In Figure 12, in addition to the “silent connect” button, TAs can use the “inject” button to show the overlay page to the infected device. Once TAs have received the list of the apps installed inside the victim device, they can upload the specific overlay page (composed of HTML, CSS, and Javascript code) to the “injections settings”, specifying the package name of the targeted app, as shown in Figure 16.

Furthermore, TAs can steal SMS messages using the “SMS RAT” capability, considering that some banks/crypto apps use the SMS as a 2FA method to send the OTP code during the login phase or to approve a transaction. When an attacker presses the “SMS RAT” button (1), on the infected device appears a popup or a setting page (depending on the Android version) that asks the user to change the default SMS manager app (2) with the malicious app (masqueraded behind the bank name/icon). In case of change, the TAs can receive all the SMS messages (3) and automatically hide them on the infected device.

Another feature available inside the panel is the “Push Notification”, probably used to send to the infected devices fake push notifications that look like a bank notification to entice the user to open the bank's app in such a way that the malware can steal credentials. As shown in Figure 18, TAs can customise the fake push notification with a “title”, a “description”, the package name of the app, and an icon.

TAs can access a specific section of the panel to create and customise malicious apps. As illustrated in Figure 19, TAs can select the names and package names for the app and specify the icon to be used. Based on past campaigns, Copybara TAs typically opt for names and icons resembling those of Italian and Spanish banks, often incorporating terms like “Token” and “Sicuro/Seguro”.
Within the panel, TAs can further customise the APK file by:

The emergence of On-Device Fraud (ODF) represents a significant and evolving threat within the realm of banking fraud. Our investigation into a recent Copybara operation sheds light on the intricate tactics employed by TAs to compromise user devices and perpetrate fraudulent activities directly through familiar channels. Using remote control functionality embedded within modern Android banking trojans, such as Vultur, TeaBot, and SpyNote, perpetrators have effectively minimised detection by challenging traditional anti-fraud measures.
Stakeholders within the banking and cybersecurity sectors must recognise the gravity of ODF and its implications for financial institutions and end-users. By understanding the complexities of these attacks and remaining vigilant against emerging threats, organisations can proactively mitigate risks and safeguard against potential losses. Our findings underscore the necessity for continued collaboration, innovation, and adaptation in the ongoing fight against banking fraud.
Collectively, we can work towards a more secure digital ecosystem for all through ongoing vigilance, robust defences, and informed decision-making.
The following table will summarize the list of all the commands found on Oscorp during the technical analysis: