In June 2025, the Cleafy Threat Intelligence team investigated a large-scale fraud campaign leveraging PlayPraetor, an Android RAT that facilitates On-Device Fraud (ODF) by giving operators complete real-time control over compromised devices. The PlayPraetor campaign, initially detailed by CTM360, has been active for several months, strategically impersonating legitimate Google Play Store pages to trick victims into downloading malicious applications. Cleafy's investigation has revealed the underlying Malware-as-a-Service (MaaS) operation carried out by TAs, which has infected over 11,000 devices globally in less than three months.
The operation is managed via a sophisticated Chinese-language C2 panel featuring a multi-tenant architecture that enables multiple affiliates. This structure has allowed the campaign to achieve significant global reach, though with a highly strategic focus. Europe is the primary target, accounting for 58% of all infections, with high concentrations of victims in Portugal, Spain, and France. The campaign also has a notable presence in Africa (with Morocco as a hotspot), Latin America (with high presence in Peru), and Asia (primarily Hong Kong). The affiliate network is dominated by two principal operators who control roughly 60% of the botnet and seem to be specialised in Portuguese-speaking targets. In contrast, other smaller affiliates focus on different language demographics, such as Chinese, Spanish, and French-speaking victims.
The botnet is expanding at a rate of over 2,000 new infections per week, and recent data signals a clear strategic pivot in targeting. While infections among its traditional victim base are decelerating, operators are aggressively pursuing new campaigns against Spanish and French speakers, posing a significant and escalating threat to financial institutions and their customers in Spain, Latin America, and French-speaking regions.
This strategic expansion is made possible by the effective application of the PlayPraetor RAT, which uses common and well-established techniques for ODF. By abusing Android's Accessibility Services, the operators gain real-time control of the infected device. An investigation of the overlay attack payloads revealed an extensive list of global targets, including nearly 200 banking apps and cryptocurrency wallets. Cleafy's analysis revealed the presence of new commands for the RAT, evidence of the continuous development of the latter, showing that the developers are actively maintaining their toolset to ensure its effectiveness.
The mobile threat landscape continues to evolve, with widespread campaigns employing techniques to bypass traditional security measures and compromise users. A notable example of this escalating threat is the PlayPraetor campaign, a global operation first detailed by CTM360. This campaign strategically impersonates legitimate Google Play Store pages, tricking victims into downloading malicious applications or revealing sensitive information.
While using fake Play Store pages to deliver malware is a well-established tactic among cybercrime groups, the truly significant aspect of these campaigns lies in their scale. Initially, it was identified as a localised threat, as the RAT disguised itself as some legitimate banking institutions. Subsequently, the campaign underwent significant expansion, using more than 16,000 URLs and employing various techniques to profit from victims. This evolution marks a clear transition from a regional to a global threat. CTM360 has identified five variants of these campaigns, each with distinct attack capabilities:
Cleafy's investigation into this threat began with acquiring the first malware sample of the Phantom variant in April 2025. This initial sample, originating from a deceptive Play Store page, provided crucial early insights into the malware's distribution channels and confirmed the central role of fake Play Store pages in its delivery strategy. A month later, a significant spike in the malware's activity was observed in Southern Europe and LATAM, prompting Cleafy to investigate the malware's characteristics and underlying infrastructure.
This investigation focuses only on the Phantom variant, which will be referred to simply as PlayPraetor in this report.
PlayPraetor is a modern Android RAT. Its core functionality relies on abusing Android's Accessibility Services to gain extensive, real-time control over a compromised device. This allows an operator to perform fraudulent actions directly on the victim's device.
PlayPraetor implements a communication strategy that utilises three distinct protocols to maintain robust control. The malware establishes an initial connection using a resilient heartbeat mechanism over HTTP/HTTPS. It iterates through a hardcoded list of C2 domains, sending a heartbeat request to the /app/searchPackageName path upon activation. This iterative process ensures resilience against takedowns by retrying the next domain if the current one is unresponsive.
Once a connection is live, the following channels are used for real-time control and monitoring:
The WebSocket channel is the primary method for command and control. The main command types are outlined below:
Further analysis of the malware reveals an active and ongoing development, with notable divergences when compared to the initial versions detailed by CTM360. This is immediately evident in the main command structure. Key commands present in this version, such as heartbeat_web for maintaining a stable WebSocket connection and report_list for dynamically updating the list of targeted applications, were absent in the earlier samples. As detailed in the Appendix, this evolutionary trend is also visible at a more granular level within the malware's sub-commands. Key changes between the February and June 2025 samples include:
While WebSocket and RTMP are used for real-time control, the HTTP/S protocol is the primary channel for exfiltrating data harvested from the victim's device. Our analysis identified several specific API paths used for this purpose:
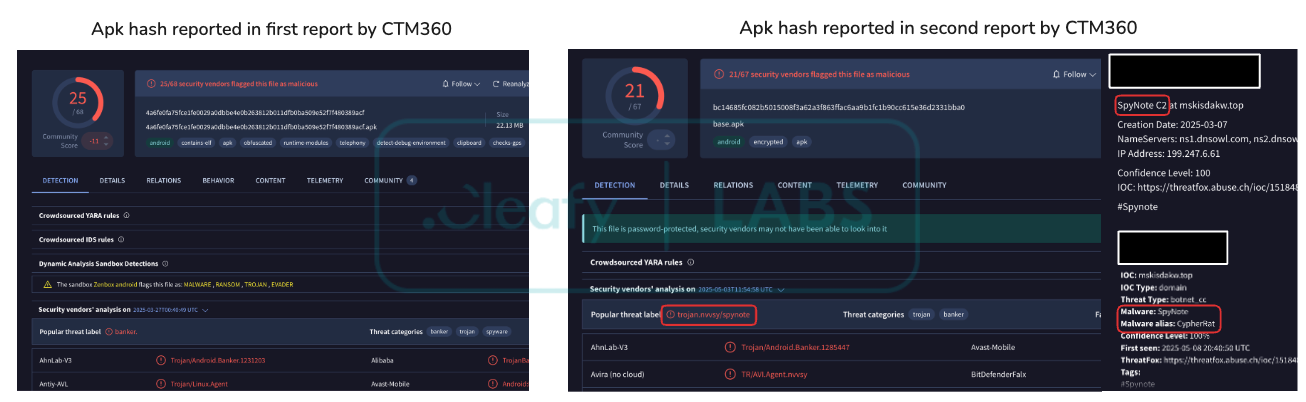
Before concluding this section, it is important to address a general observation regarding the classification of C2 infrastructure and related malware samples on public threat intelligence platforms. It’s worth mentioning that samples from the PlayPraetor family have sometimes been misidentified and categorised under an unrelated malware family, likely due to a vast network of interconnected fraud campaigns. Analysis of those infrastructures revealed that multiple concurrent operations employed various distinct malware families, including the PlayPraetor RAT, which is the focus of this analysis, and others such as SpyNote. Discussing these different malware tools within the same report led some public threat intelligence platforms to conflate them, resulting in PlayPraetor samples being erroneously tagged as SpyNote, as shown in the example below.
Our in-depth investigations into the PlayPraetor campaigns, conducted in June 2025, reveal a significant and evolving threat. More than 11,000 devices have been compromised in less than three months, demonstrating this Android RAT's substantial reach and impact. To better understand which regions are most impacted and identify future threats, this analysis evaluates the profile of typical target victims. By examining these patterns, we aim to provide valuable insights into the operational strategies driving these attacks. The malware's distribution via a MaaS model, a widely common approach in recent years, also allows us to delve into the activities of individual affiliates. This enables us to identify specific targets and discern operational patterns unique to each affiliate, offering a detailed view of the threat landscape and potential future trends.
The PlayPraetor botnet exhibits a remarkable global reach, with infected devices spanning multiple continents. However, a deeper analysis reveals that this is not a campaign of random, widespread infection, but rather a series of highly concentrated, strategic operations focused on specific linguistic and geographical regions.
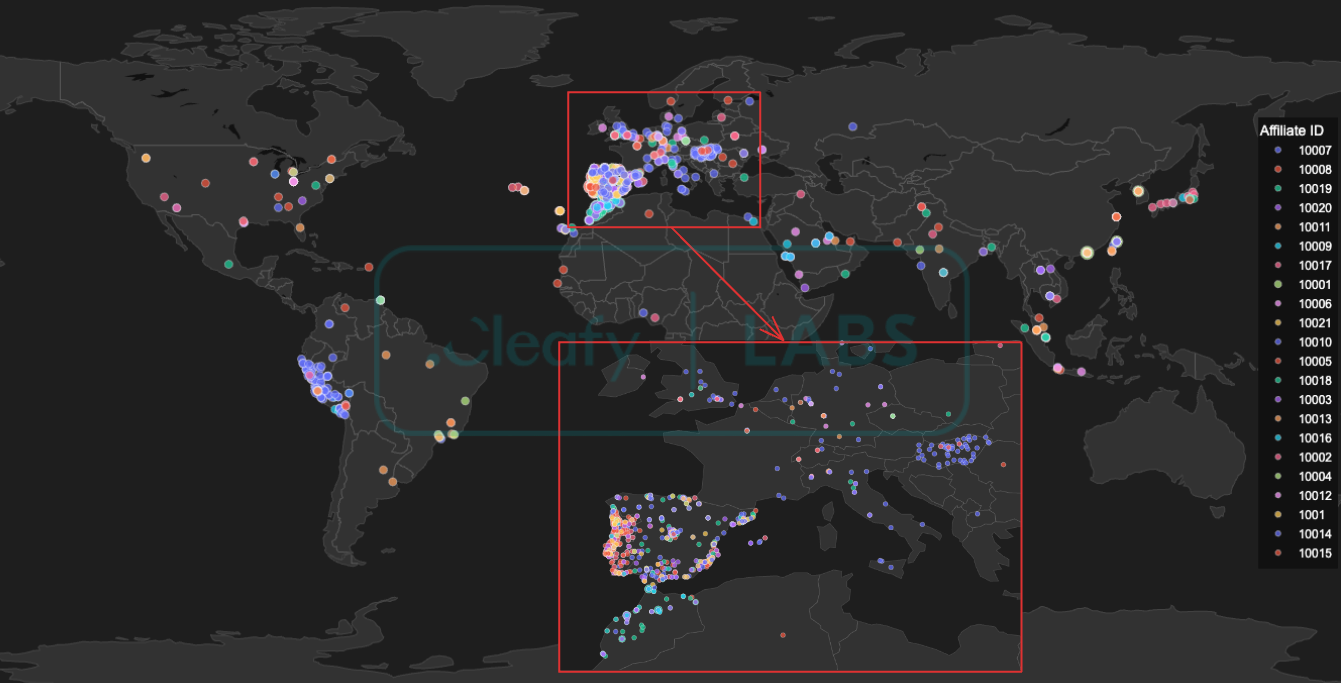
Based on the victim's IP addresses, the global infection map provides a clear visualisation of this strategy. The data overwhelmingly indicates that Europe is the primary operational target, representing 58% of all compromised devices. This is visually confirmed by the dense clustering of infection points across the continent, with particularly high concentrations visible in Portugal and Spain. This geographical focus aligns perfectly with a calculated linguistic targeting strategy, with Portuguese and Spanish being the most targeted languages. France, Hungary, and Italy are among the other highly impacted European countries.
While Europe is the main target, other continents show signs of similarly focused efforts. Accounting for 22% of total infections, the botnet's footprint in Africa is characterised by a geographically dispersed activity, with the clear exception of Morocco, which has emerged as the continent's primary hotspot. The Americas (12%) see a higher concentration in South America, with Peru standing out as a main target. Finally, Asia (8%) shows notable infection clusters in East and Southeast Asia, corroborating IP data that highlights significant activity in Hong Kong.
This targeted proliferation of infected devices is further illustrated in the backend dashboard of the attacker’s C2 panel.
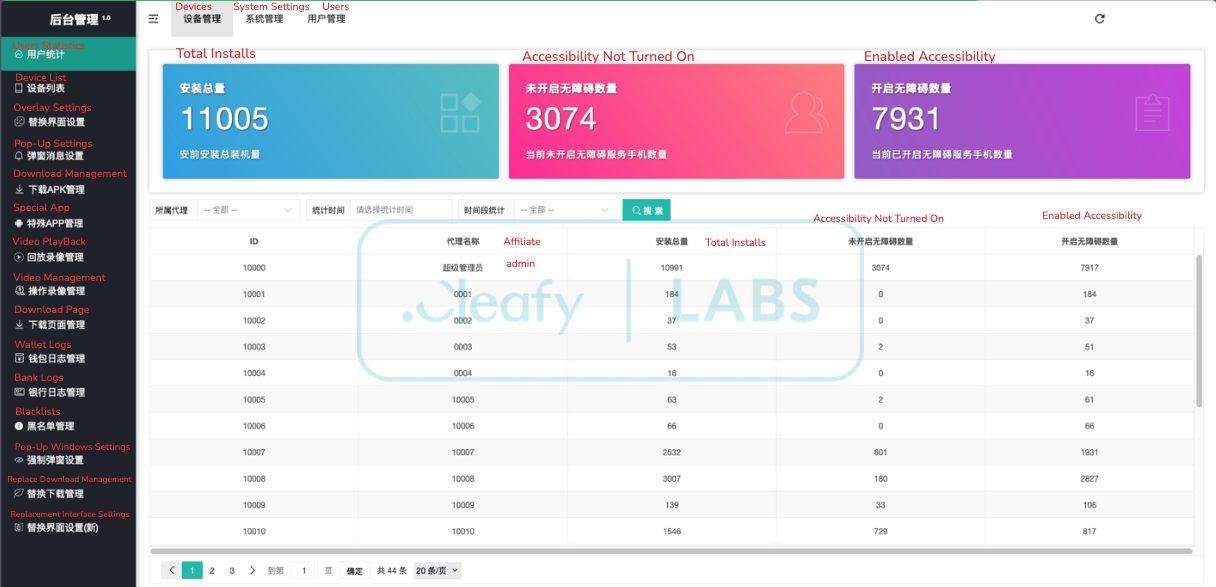
The C2 panel shows 11,005 total installations, but more importantly, 7,931 of these devices have enabled the malware's required Accessibility service. This represents a good activation rate of 72%, signifying that nearly 8,000 devices are fully "armed" and under the operators' control. Consequently, our analysis will concentrate on this pool of fully operational threats.
The botnet's affiliate structure provides critical insights into its operational hierarchy and strategic priorities. The network's control distribution is skewed, revealing a two-tiered system composed of a few dominant affiliates and numerous smaller, more specialised ones.
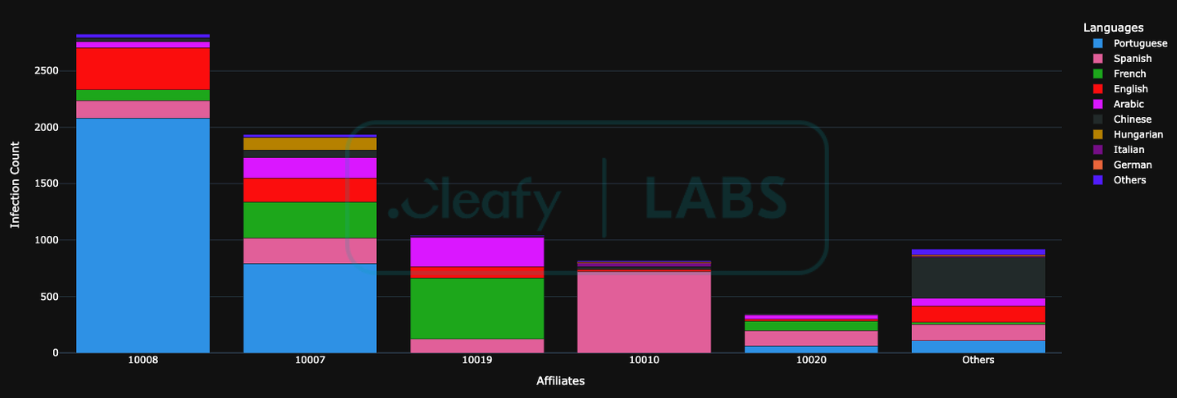
This imbalance is quantitatively illustrated in Figure 4, which details the absolute infection volume managed by each affiliate. The network is predominantly controlled by two principal affiliates, 10008 and 10007, which collectively command more than 4,500 compromised devices. This represents almost 60% of the botnet, specifically among devices with accessibility services enabled. Furthermore, the operational focus of these dominant affiliates is clearly defined, with Portuguese-language devices (represented by the Azure segment) comprising the most significant proportion of their respective victim pools. While Figure 4 demonstrates volume, an analysis of the normalised targeting strategies, presented in Figure 5, elucidates the distinct operational specialisations. This proportional view highlights how each affiliate allocates resources across different language demographics.
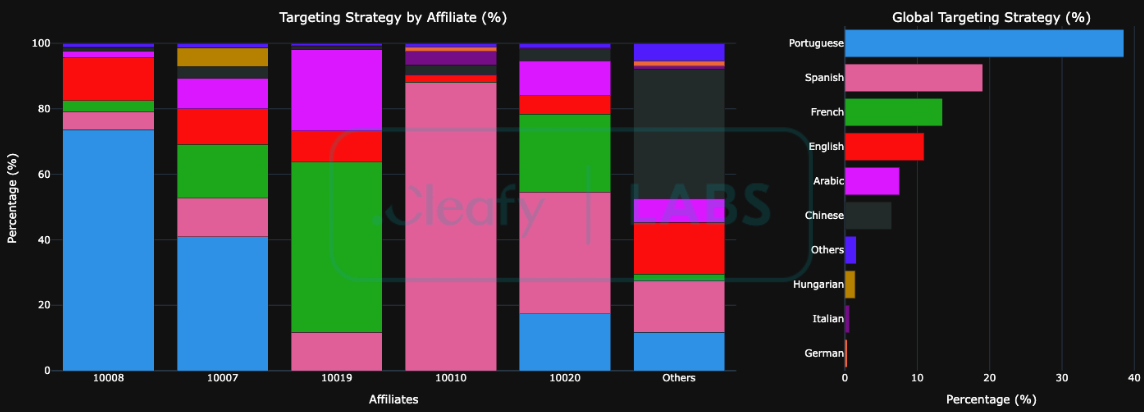
This proportional view reveals several distinct operational archetypes based on their targeting strategy:
While predicting the botnet's future evolution is speculative, analysing temporal trends in new infections reveals emerging strategic shifts. The data, illustrated in Figure 6, shows a dramatic spike in activity in late June 2025, with new infections surging to over 2,000 compromised devices in the final week. More importantly, this growth is highly uneven and clearly indicates a radical shift in targeting priorities.
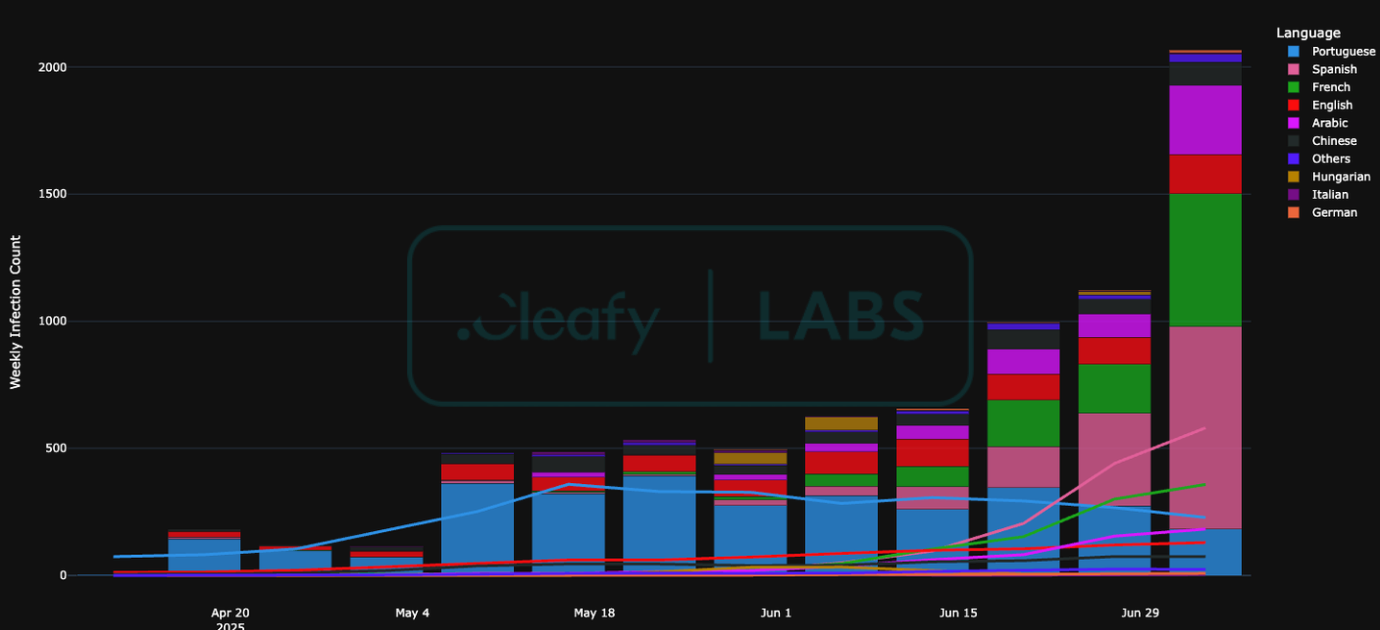
The most significant development is the exponential growth in Spanish-speaking victims (pink). After being a secondary target for months, this demographic became the primary driver of the botnet's expansion in late June, accounting for the largest share of new infections. This trend poses a significant and rapidly escalating risk for users in Spain and Latin America. This surge in Spanish targets coincides with a deceleration in new infections among Portuguese speakers (blue). This directly supports the hypothesis of a strategic pivot: the core affiliates, focused on the now-stagnating Portuguese market, appear to be ceding ground to other affiliates who are expanding into new territories.
This is further supported by the sustained, significant increase in French-speaking victims (green), which now represents the second-largest source of new weekly infections. Meanwhile, the number of English (red) and Chinese (black) targets remains relatively stable, positioning them as consistent but lower-priority operational theatres. A final, telling development is the sudden, sharp spike in Arabic-speaking victims (purple) in the last week, which may signal the opening of another major campaign front.
The PlayPraetor C2 panel serves as the central operational hub for the TAs, allowing them to manage and exploit compromised devices. Analysis of the panel interface reveals a sophisticated and well-organised system, primarily presented in Chinese. This suggests that the core development and operational team behind PlayPraetor is likely Chinese-speaking.
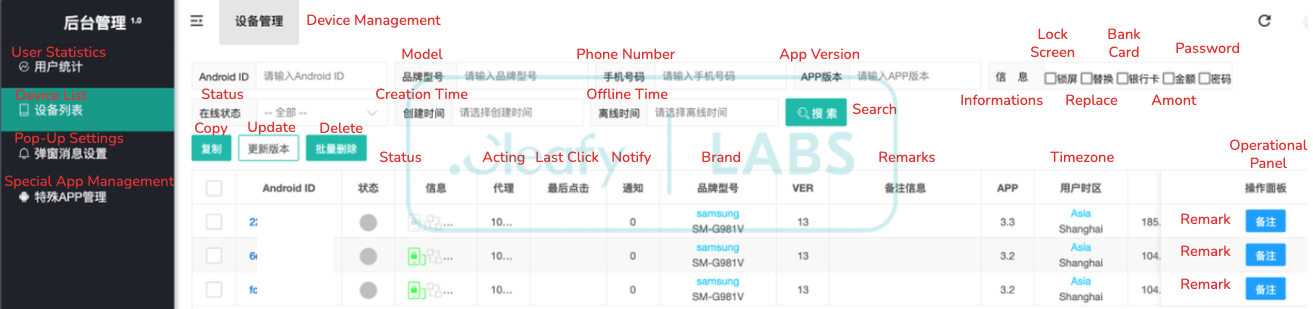
The panel is designed with a "multi-tenant" architecture, meaning it supports separate environments or "tenants" for each individual affiliate. This multi-tenancy enables the distinct affiliates, as identified in the botnet affiliate structure, to manage their specific victim pools and campaigns independently while leveraging a shared, robust infrastructure.
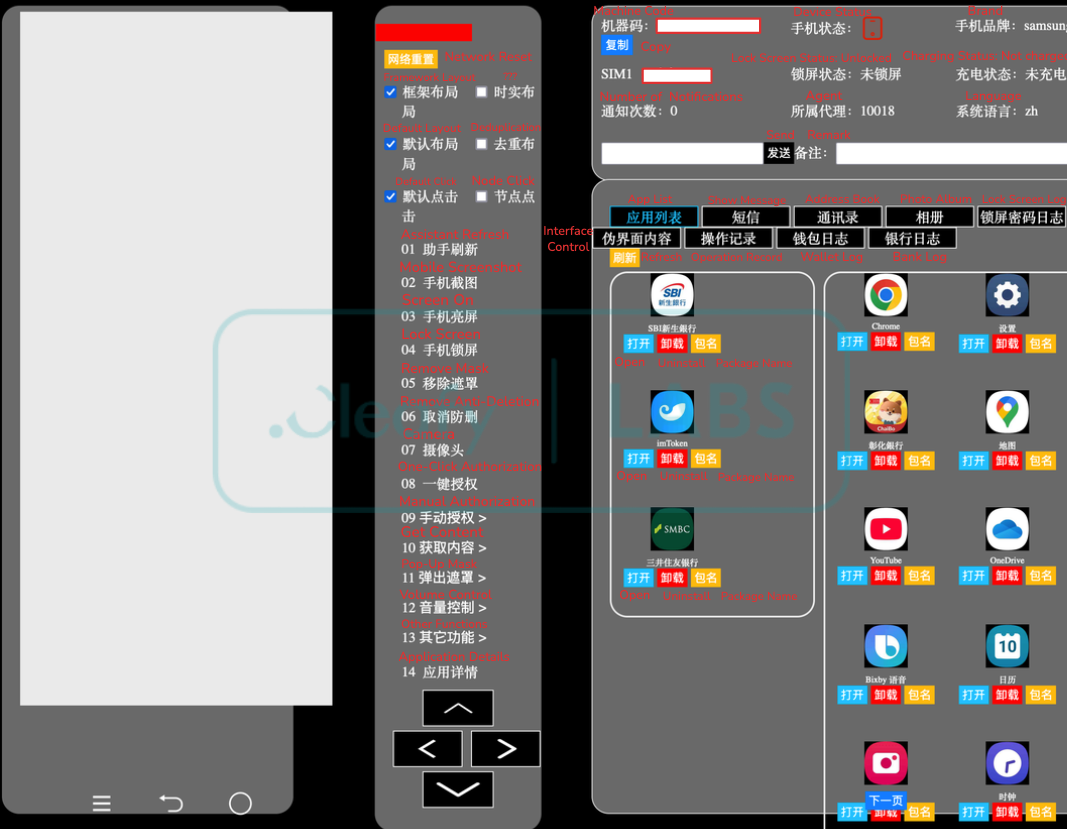
A key component of the PlayPraetor panel is the device remote control section, which allows operators to actively interact with compromised devices in real-time. As shown in the panel's interface (Figure 8), this functionality extends beyond simple commands, providing a suite of interactive tools for a complete device takeover. This empowers the operator to actively impersonate the victim, enabling direct ODF. At the top, a status bar provides the operator with essential device information, including its unique ID, battery level, and connection state. To the left, a vertical command menu offers a powerful suite of interactive tools, including functions to stream the device’s screen in real-time, capture screenshots, and even access the device's camera. The central component of the dashboard is a grid displaying all applications installed on the device. This provides the primary attack surface, allowing the operator to launch any app with a single click. This capability, combined with a row of buttons for viewing exfiltrated personal data, such as lock screen passwords, past notifications, and logs of overlay attacks, creates a powerful environment for fraud.
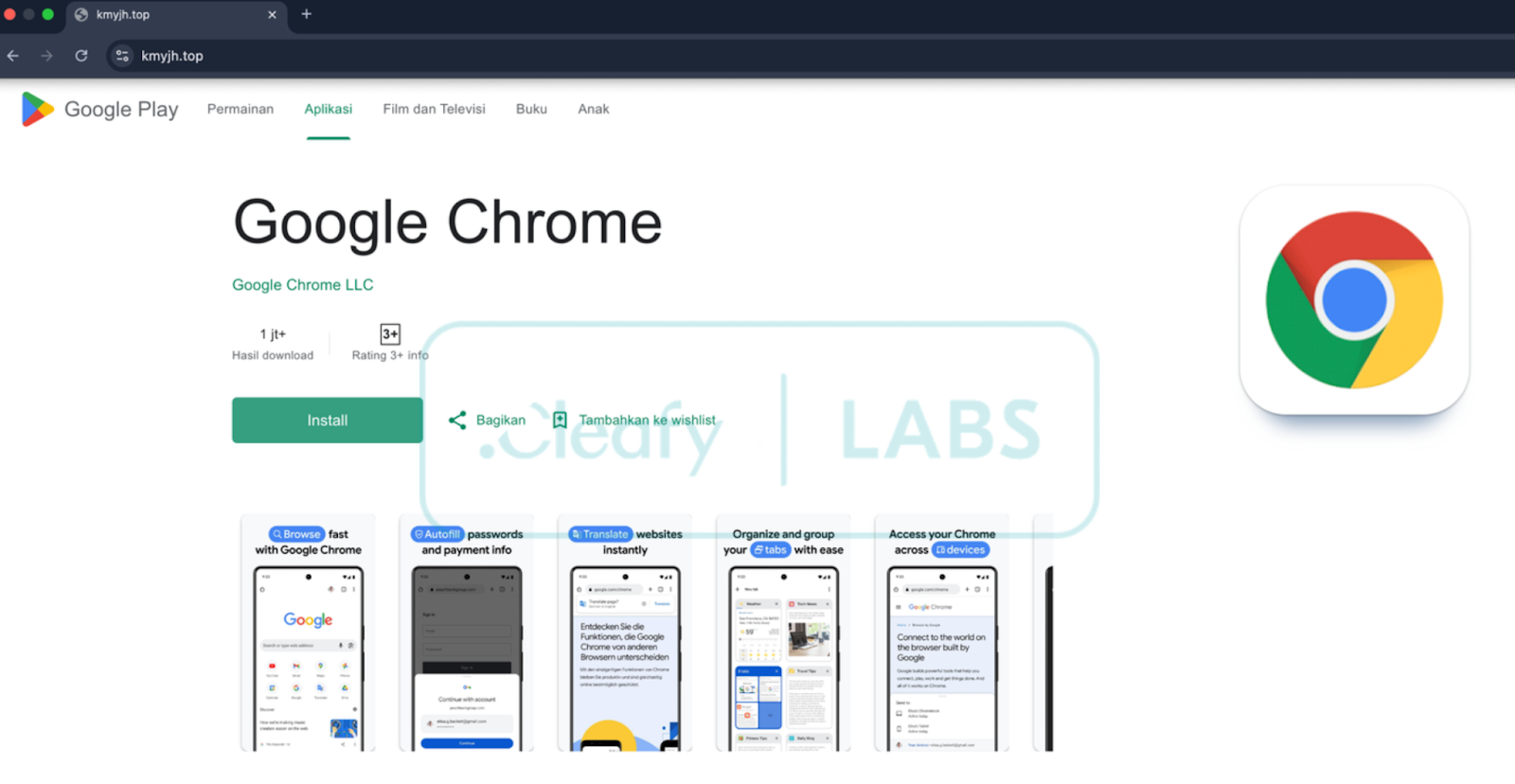
The panel interface reveals that this infrastructure is used not only to manage infected devices but also to orchestrate the malware delivery campaign itself. A dedicated section within the panel is specifically designed to create and administer decoy landing pages that convincingly mimic legitimate platforms, like the Google Play Store. As shown in Figure 9, the panel provides a detailed configuration interface for generating these phishing pages. The example highlights the creation of a page impersonating the official Google Chrome download page. Operators have granular control over the content, allowing them to define a custom domain (e.g., kmyjh[.]top), a page title, and a descriptive text. Furthermore, they can upload related visual assets, such as the application's icon and carousel images, to enhance the page's authenticity and deceive potential victims.
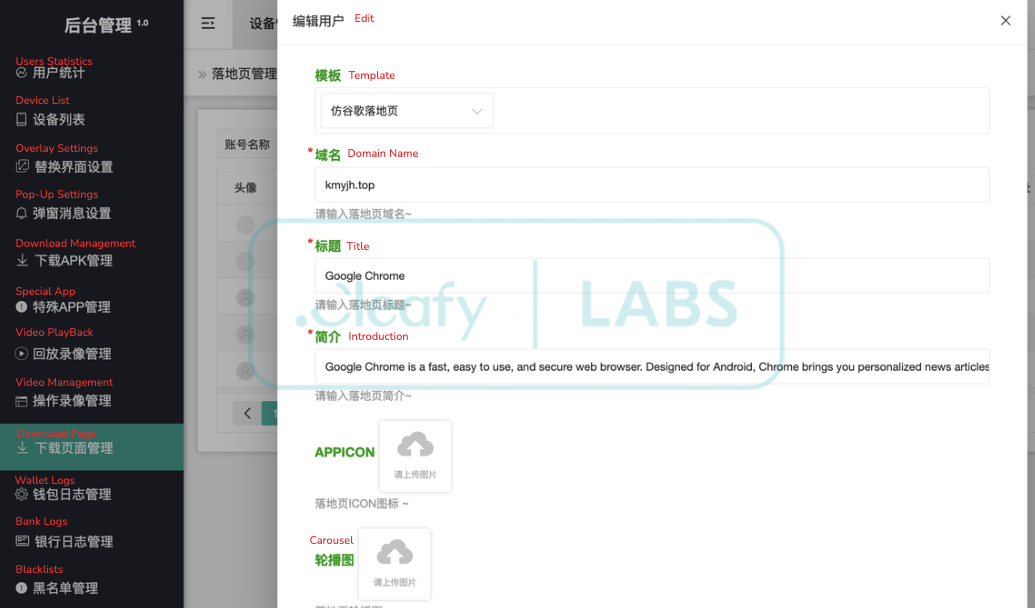
This functionality strongly indicates that the phishing infrastructure is built to be modular and highly customizable. This likely enables operators to quickly generate and deploy fake download pages for various well-known and trusted applications, adapting their campaigns to different targets or opportunities. It is also worth noting that the schema suggests the domain setup is managed manually: the panel allows operators to insert pre-registered domains rather than dynamically provisioning them. This implies a clear separation of concerns within the operation, distinguishing the rapid creation of phishing content from the more complex setup of the underlying domain infrastructure.
The operators behind PlayPraetor have established a sophisticated and highly effective fraudulent operation that has achieved a remarkable global scale, infecting over 11,000 devices. The campaign's success is built upon a well-established operational methodology, leveraging a multi-affiliate MaaS model. This structure allows for broad and highly targeted campaigns, which are now expanding at over 2,000 new compromises per week.
PlayPraetor represents another significant entry from Chinese-speaking threat actors into the global financial fraud landscape. This trend, exemplified by recent campaigns such as ToxicPanda and Supercard X, demonstrates an increasing interest from TAs in this region in developing and deploying sophisticated attack vectors against financial institutions worldwide. While technically PlayPraetor does not deviate from other modern Android banking trojans, implementing well-established techniques for On-Device Fraud through the abuse of Android's Accessibility Services, its innovation lies in its operational model.
The authors have established a robust business model that enables global distribution through independent campaigns managed by different affiliate groups. Furthermore, directly integrating campaign creation and management functionality within the C2 panel represents a significant operational advancement. This centralisation enables affiliates to manage all phases of the kill-chain from a single control interface, dramatically simplifying operations and lowering the barrier to entry for new affiliates.
Cleafy's analysis confirms PlayPraetor is undergoing continuous adaptation, evidenced by changes in its commands designed to enhance evasion and expand functionality. In summary, combining a scalable MaaS platform, streamlined campaign management tools, an adaptable operational strategy, and a constantly improving RAT makes the PlayPraetor campaign a dynamic and highly relevant threat to the global financial ecosystem.
This report is a TLP:WHITE version intended for public dissemination and is based on an original TLP:AMBER report. The TLP:AMBER report was previously shared privately with relevant financial CERTs, impacted banking institutions, and law enforcement agencies (LEAs).
We encourage trusted researchers and analysts within the community to contact us at labs@cleafy.com to request access to the TLP:AMBER version. Access will be granted to those recognised as "trusted entities," allowing for a deeper insight into the findings and supporting data behind this analysis.
Malware samples:
C2 Infrastructure:
Delivery Page:
Be among the first people worldwide to receive comprehensive technical reports on newly uncovered threats.
Subscribe now